Introduction
| Top |
|
Data Masking |
Content |
|||||||||||||||||||||
|
Introduction |
|
|
To comply with PII, PHI, HIPAA, and Safe Harbor requirements, and to protect the privacy of individuals, you may need to hide or mask sensitive information from unauthorized Users within LabVantage. Data Masking is a highly configurable solution that automatically determines who is authorized to view sensitive information and who should be shown masked information (based on existing Security measures and policy decisions).
When an unauthorized User is presented sensitive information, LabVantage determines how the information should be displayed to that User.
The example below illustrates a typical Data Masking strategy.
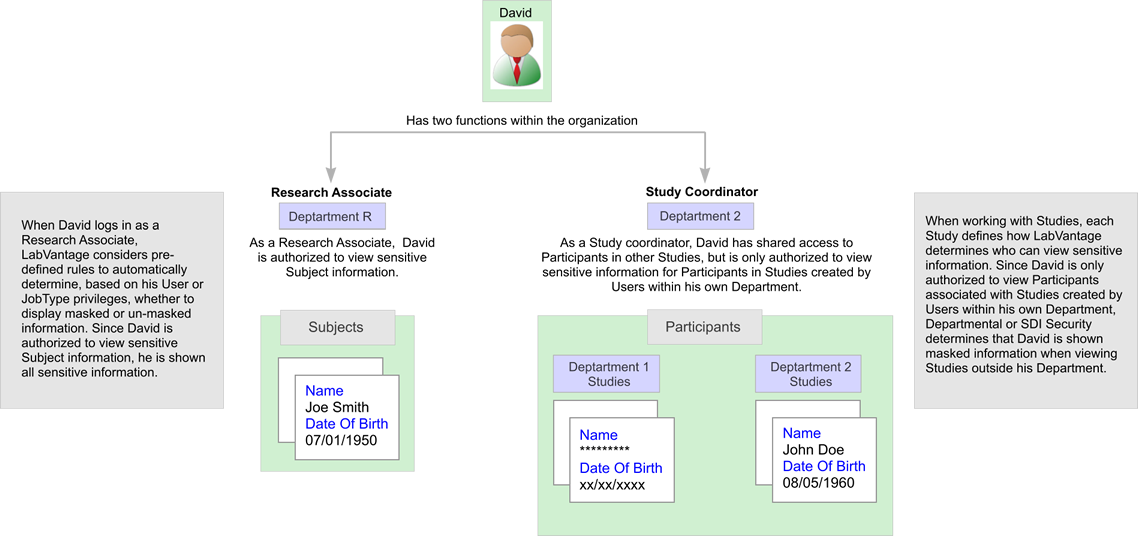
|
Before you configure Data Masking, consider the following for your organization:
Identify the SDCs (such as Subject) that contain sensitive information. Within that SDC, which columns are sensitive (such as birthdt).
When presented to unauthorized Users, how should sensitive information be masked. Define different masking techniques (such as ***-**-1234) for each column. Optionally, define different levels or degrees of masking. These Levels can be specified at the SDC or SDI level (such as during Study creation on a Study by Study basis) and therefore determine how Data Masking is applied for each SDI.
OOB, LabVantage provides masking templates you can customize according to your preferences.
Identify the Users or JobTypes authorized to view sensitive information, and under what circumstances. Visibility Rules identify authorized Users using one of the following methods:
| • | By Role Only Users with the specified Role are authorized to view sensitive information. Users without this Role will see masked information. |
| • | By Department or SDI Whether or not a User is authorized to view sensitive information is determined by existing SDI or Department Security settings. For example, any User within Department 1 can view sensitive information within a Study created by any other User within Department 1. Users in Department 2 are not authorized to view sensitive information for that Study. |
| • | Using Limited Data Access SQL to create custom access for a specific User. |
To configure Data Masking within LabVantage you will need to:
| • | Enable Data Masking for each SDC that contains sensitive information. |
| • | Define the Masking Policy. Use the MaskingPolicy to specify, for each column deemed sensitive, the techniques to use when information is shown to unauthorized Users. Define and specify any Masking Levels (such as High, Medium or Low). |
| • | Choose Visibility Rules that tell LabVantage how to determine which Users are authorized to view sensitive information. |
Enable Data Masking for an SDC |
|
|
Before defining Data Masking policy you must first decide which SDCs contain sensitive information. Once decided, you will need to enable Data Masking for those SDCs. Doing so makes the SDCs available in the Masking Policy where you will define Masking Levels, Masking Rules (techniques) and Visibility Rules.
| NOTE: | OOB, data masking is configured for the Biobanking module. You can optionally turn data masking on for any SDC by checking the "Contains Sensitive Data?" option as described below. |
Navigate to System Admin → Configuration → SDCs. The SDC List Page displays. Select an SDC and click "Edit" to open the Edit SDC page.
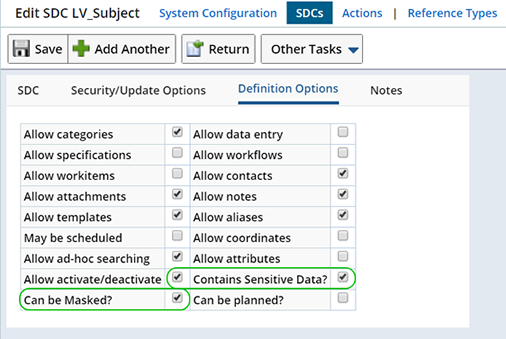
In the Definition Options detail you will find the "Contains Sensitive Data?" and "Can be Masked?" fields. These are used to enable Data Masking.
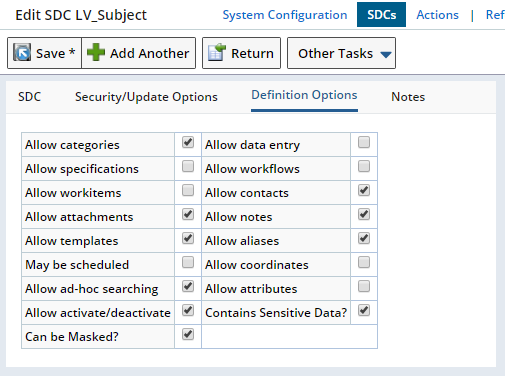
| Field | Description | ||||||||||||
| Contains Sensitive Data? | Determines whether or not this SDC contains sensitive information.
Checking this option makes this SDC available in the MaskingPolicy where you can define Masking Rules.
If sensitive information is not stored on an SDC (such as a Sample), but sensitive information may at some point be associated with that SDC (an associated Subject), choose to leave this option unchecked (no need to define Masking Rules), then check "Can be Masked?" below. This ensures that any associated sensitive information is automatically masked when viewing the Sample (according to the associated SDCs Masking Rules). |
||||||||||||
| Can be Masked? | Determines whether or not sensitive information contained within this SDC will be masked. When checked, information deemed sensitive (in the Masking Policy) will be automatically masked according to defined Masking Rules.
This means that if at any point sensitive information contained within the SDC is displayed to an unauthorized User, the Masking Policy will be applied.
This includes:
When unchecked, sensitive information will not be masked for this SDC. |
Define Masking Policy |
|
|
Use the MaskingPolicy to configure your Data Masking strategy. Determine the fields within an SDC that contain sensitive information, the techniques for masking that information, and how LabVantage will determine authorized Users (those Users for whom sensitive information will be un-masked).
To define the Masking Policy, navigate to System Admin → Configuration → Policies and choose "MaskingPolicy".
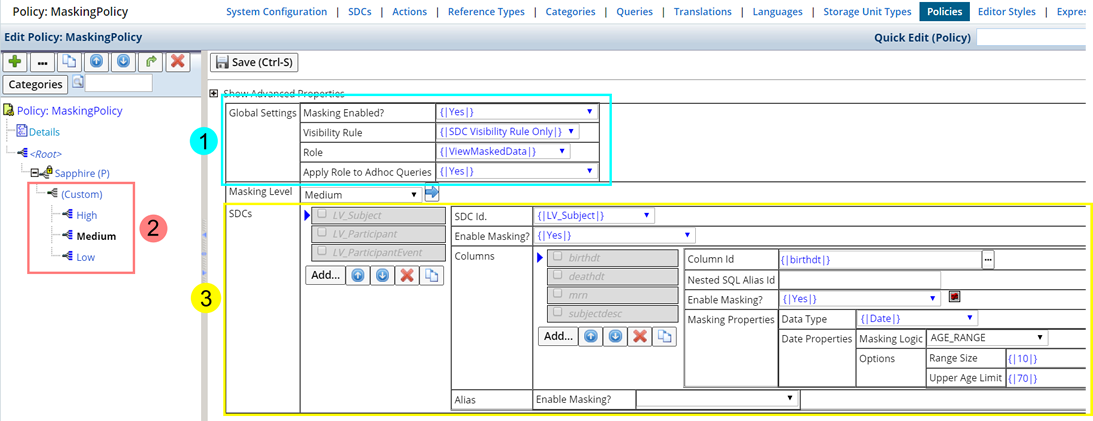
| 1 | Global Settings |
| 2 | Masking Levels |
| 3 | Masking Rules (Techniques) |
Global Settings |
The Global Settings Properties of the Masking Policy determine how Data Masking is implemented throughout LabVantage. These settings determine whether or not sensitive information will be masked, and to whom.
| NOTE: | It is important to make these changes in the Sapphire Custom node. Any changes made to these values at the individual node level will have no effect, as these are Global settings. |
| Property | Description | ||||||||||
| Masking Enabled? | When "Yes", Data Masking is enabled throughout labVantage. Global Masking Rules are applied to sensitive information within those SDCs defined with the "Contains Sensitive Information" option checked. | ||||||||||
| Visibility Rule | Specifies how LabVantage should determine which Users can view sensitive information.
The Visibility Rule uses the existing Security structure (such as Role, Department Security or SDI Security) to enable visibility by individuals or groups of Users.
|
||||||||||
| Role | The Role Users must have in order to view sensitive information. | ||||||||||
| Apply Role to Adhoc Queries | When "Yes" the specified Role (above) will be used to enforce the Masking Policy in Adhoc Queries. The default is "Yes". |
To define a more complex, SDC specific, Data Masking plan choose one of the SDC Visibility Rules and define a Visibility Rule at the SDC level. See SDC Level Data Masking for more information.
Masking Levels |
Optionally, pre-define different levels of Data Masking (such as highly restricted or minimally restricted) using the Masking Level field. The value selected in this field identifies the level for which the displayed Masking Rules are defined. If no Masking Level is defined (blank), the defined rules are the default, or global Masking Rules. See Define Masking Rules for more detailed information.
These Levels are available when creating SDCs and SDIs, providing the ability to define a different level of Data Masking for an SDC, or on an SDI by SDI basis. For example:
| Studies A and B might consider a Subject's Name, Date of Birth and Medical Record Number (MRN) to be sensitive. Study creators can choose a pre-defined Data Masking Level of High during Study Creation. | |
| Study C might only require that a Subject's Medical Records Number (MRN) be considered sensitive and will choose a Low Masking Level. |
To accomplish this, you will need to define different sets of Data Masking Rules and techniques for each defined level. These levels can then be specified for an SDC (and will default to the SDI), or specifically for an SDI (override the default). LabVantage determines which Masking Level to apply in the following order:

When not defined at the SDC or SDI level, settings defined in the Masking Policy (Sapphire Custom node) are applied.
| NOTE: | When defining Masking Levels be sure to set the "Copy Masking Level" property in the Copy Down Policy to "Yes". This ensures the Masking Level is copied to SDIs. |
If you do not intend to define Masking Levels skip to Masking Rules for details about defining Masking Rules and techniques.
| Define Different Masking Levels |
Masking Level values (such as High, Medium or Low) are defined as values in the Masking Level Reference Type. High, Medium and Low are provided OOB however you can establish your own Masking Level values.
Each Reference Type links to one Node in the Masking Policy. For each Masking Level (Node) define a different set of Data Masking Rules. See Node Hierarchy for information about defining Nodes.
| Specify Each Level |
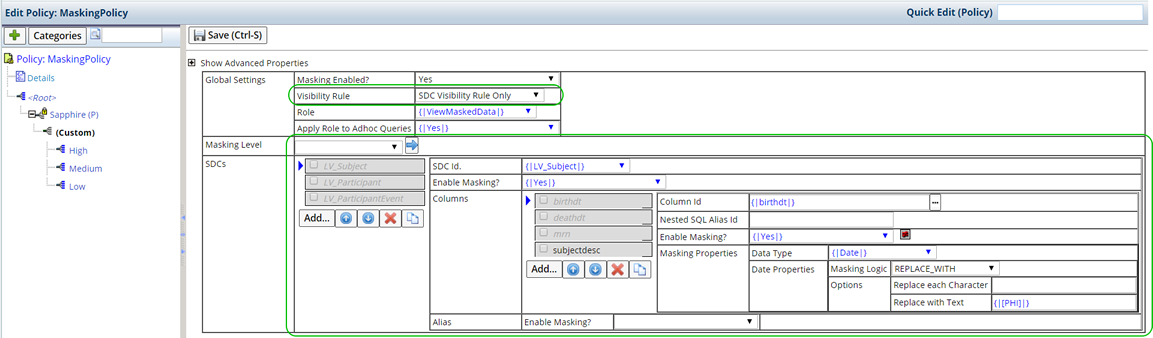
In the Masking Policy, choose a Masking Level Node (such as High, Medium or Low), and then the SDC and Column. Define the Masking Rules associated with that Masking Level, SDC, and column combination. Leaving the Masking Level blank defines Global Masking Rules.
Select the Node (as defined by the Reference Type Values). Note that the Masking Level field fills with the corresponding Level.
This example defines a High Masking Level for the Subject SDC, "birthdt" column. See Define Masking Rules below for more information about defining Masking Rules.
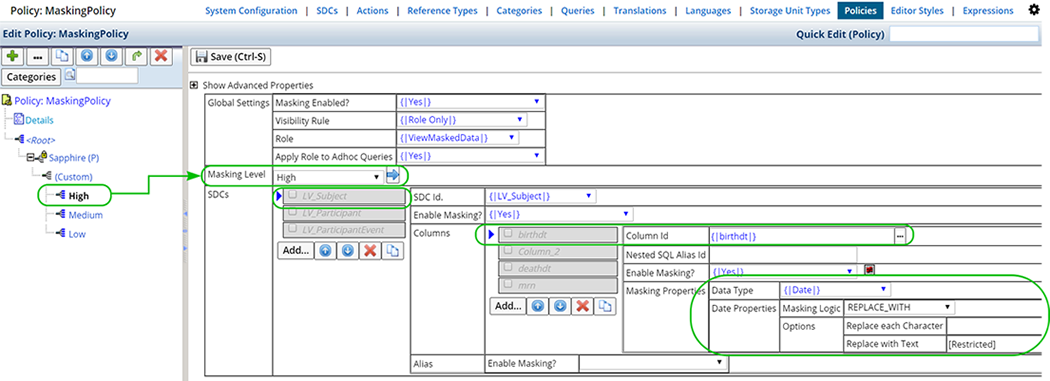
In the following examples, the Medium and Low Masking Levels are defined for the Subject SDC, "birthdt" column.
| Medium Masking Level |

|
| Low Masking Level |
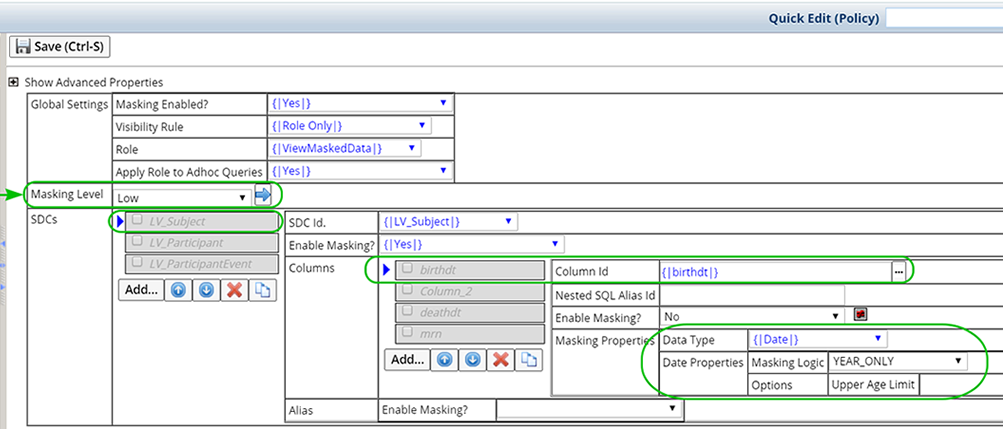
|
| Specify a Masking Level at the SDC and SDI Levels |
The Default Masking Level defined for an SDC, determines which Masking Rules to apply when displaying masked data for this SDC. Masking Levels specified at the SDC level default to SDIs.

Optionally, specify a Masking Level on an SDI by SDI basis.
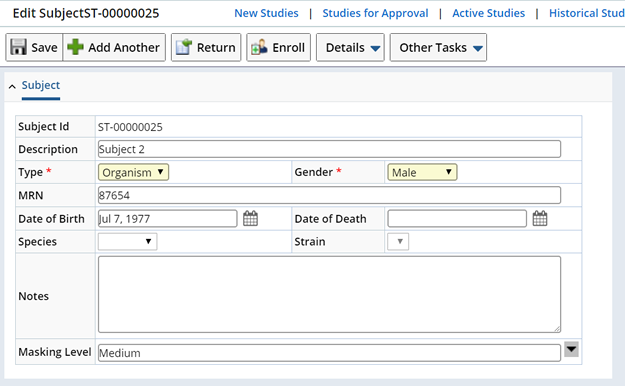
| NOTE: | You may need to expose the Masking Level field within the SDI. |
In the example below, each Subject was assigned a different Masking Level. Data is Masked accordingly to unauthorized Users. Note that "Subject 4" was not assigned a specific Masking Level and uses the global settings.
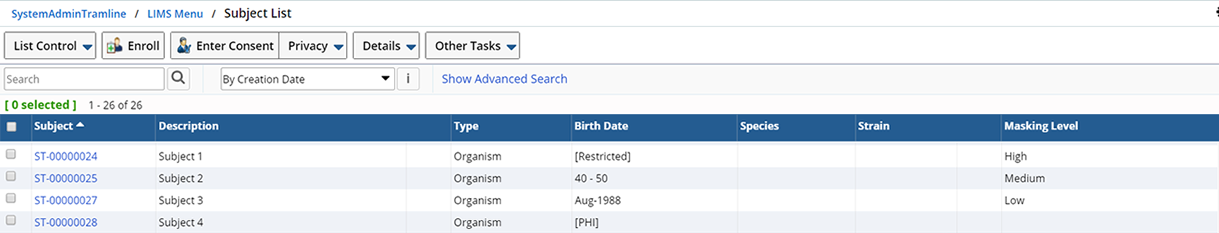
Define Masking Rules (Techniques) |
Masking Rules define how data will be masked when presented to unauthorized Users. You might choose to replace all but the last 4 digits of a Social Security Number with an asterisk, or display an age range rather than an individuals actual age.
Masking Rules can be defined in the Masking Policy for each SDC (having the "Contains Sensitive Information?" option checked).
Select the SDC for which you want to define Masking Rules, then "Add" the columns you have identified as containing sensitive information.
| NOTE: | OOB, SDCs and columns have been configured for the Biobanking module. You can enable and configure any SDC for Data Masking. |
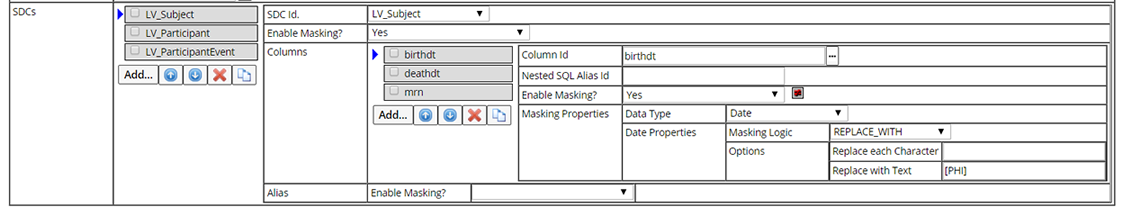
Define the following for each column.
| Property | Description |
| Column Id | Id of the column that contains sensitive information (such as birthdt). |
| Nested SQL Alias | Alias Id of the nested SQL column defined in the target element. |
| Enable Masking? | Whether or not Masking Rules will be applied for this column. |
| Masking Properties | Define how information will be masked for each type of data. See Masking Properties for detailed information. |
All supported Elements will honor the columns configured in the MaskingPolicy.
The following column formats are supported for List and Maintenance Elements:
| • | Primary SDC column Id with or without an Alias. |
| • | FK SDC column id using dot notation, such as s_subject.subjectdesc in ParticipantList page. |
| • | Nested SQL statement, such as Subject name in Sample List page. |
| NOTE: | Keep in mind that you are defining a technique for the specified SDC and column. This technique is applied when viewing sensitive information on that SDC.
These columns however may be displayed on various other pages and list pages (not just this SDC). Unless masking rules are specifically defined within the context of another SDC, the masking techniques defined for this SDC, are applied when these columns are displayed elsewhere. For example, on the Subject SDC you might decide the birthdt field should be masked with an age range, but when viewing birthdt on the Participant record, birthdt should be masked using [RESTRICTED]. If you do not define context specific masking for the Participant SDC, the Subject Masking Rules will be applied when viewing birthdt on the Participant record. See Context Specific Masking for more information about defining context specific masking. |
Masking Properties |
Field values can be treated as either Text, a Number, or a Date. For each Data Type several Masking Logic templates have been provided OOB. Use the properties below to further define each template. If no Masking Logic properties are defined, sensitive data is masked entirely, with asterisks.
| Data Type |
Choose the type of data you are Masking. Masking Properties can be defined for each of the following Data Types:
| Data Type | Description | ||||||||||||||||||||||||||||||||||||||
| Text | Logic to use when masking Text data. Mask Text data by specifying a percentage of the text to be masked, or choose to show only initial characters (Joe Smith would be shown as JS).
These are the Text Data Masking templates provided OOB:
|
||||||||||||||||||||||||||||||||||||||
| Number | Number data
can either be masked with a specified character or by a range of numbers.
|
||||||||||||||||||||||||||||||||||||||
| Date | Date fields can be masked in the following ways:
|
||||||||||||||||||||||||||||||||||||||
| Expression | Define a custom Groovy Expression. Available Variables are: value, user, primary, columnid.
For example, $G{primary.genderflag=="M"?value.replaceAll(".","*"):"Female Subject"} The above expression can be used for the subjectdesc column. It means,
if the subject is female, then show the text "Female Subject"�
or else replace every character with *. |
Alias Masking Properties |
Determine how Alias data will display when Data Masking is enabled. Field values are treated as Text.
| Property | Description | ||||||||||||||||||||||||
| Masking Properties | Logic to use when masking data. Options include specifying a percentage of the text to be masked, or choose to show only initial characters (Joe Smith would be shown as JS).
These are the Text Data Masking templates provided OOB.
|
||||||||||||||||||||||||
| Condition | Determines whether "All" Alias Types or only "Selected Types" are masked. Defaults to "All". Define the specific Alias Types to be masked below. | ||||||||||||||||||||||||
| Alias Type | Applicable when "Condition" (above) is "Selected Types". Specify which Alias Types will be Masked. |
Context Specific Masking |
Context specific masking lets you define a column as sensitive when viewed from a specific context. For example, a User with access to the Subject List page should be authorized to see all sensitive information. However, when that User accesses Subject information from a Participant list page (and context specific masking is defined), sensitive information is masked according to the Masking Rules defined for the Participant SDC.
In the Masking Policy select the SDC for which you want to create context specific visibility.

"Add" the Column you want to mask from the associated SDC. In this example, the Subject's Description field (subjectid.subjectdesc) will be masked when Subject information is displayed on the Participant List or Maintenance pages. The Subject's Name is masked using the "ONLY_INITIALS" Masking Logic, defined for the subjectid.subjectdesc column on the Participant SDC. The Subject's name (Subject 3) is displayed as S3.
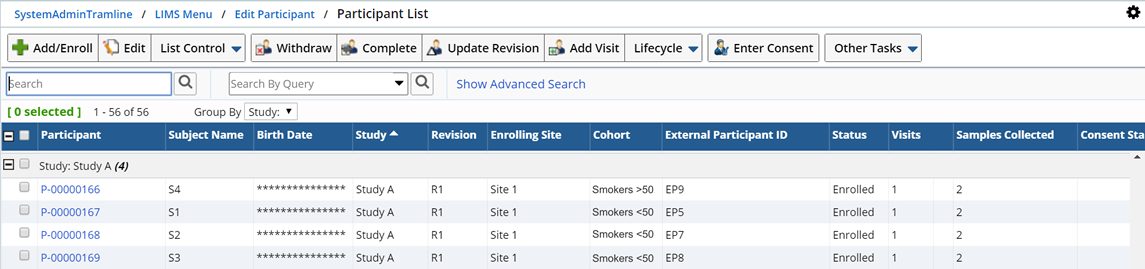
Note that the Birth Date is masked according to the global masking level, for the Subject SDC.
Define a Visibility Rule |
|
|
With sensitive information identified, and Masking techniques in place, you can now establish the Visibility Rules to "un-mask" sensitive information for authorized Users.
This section describes how to configure LabVantage to automatically determine which Users are authorized to view sensitive information.
Visibility Rules can be defined at a Global level and applied to all Users, Job Types or Departments, or specifically for an SDC. The Visibility Rule uses the existing Security structure (such as Role, Department Security or SDI Security) to authorize visibility by individuals or groups of Users.
Global Visibility Rules |
Visibility Rules defined Globally (in the Global Settings properties of the Masking Policy) apply to all Users and SDCs within LabVantage. These rules determine visibility when SDC specific Visibility Rules are not defined.
SDC Specific Visibility Rules |
SDC specific Visibility Rules determine whether or not the current User is authorized to view sensitive information for a specific SDC.
The Access Control field (and associated Security definitions such as SDC Access and Security Sets), combined with the Visibility Rule field, determine which Users can view sensitive information for this SDC.
To configure SDC specific Visibility Rules navigate to System Admin → Configuration → SDCs.
SDC Visibility Rules are defined in the Security/Update Options detail of the SDC maintenance page. When an SDC is marked as Maskable (by checking "Can be Masked?" in the Definition Options detail of the SDC) additional fields become available.
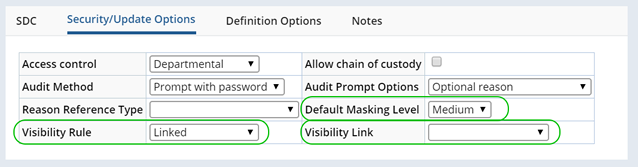
| Field | Description | ||||||||
| Visibility Rule | Choose one of the following Visibility Rules:
|
||||||||
| Visibility Link | Used when the Visibility Rule is "Linked". The Visibility Link field defines which Foreign Key link will decide the Visibility Rule for this SDC. When defining Visibility Rules for the Participant SDC for example, you might choose the Subject SDC so that Subject Visibility Rules are followed. | ||||||||
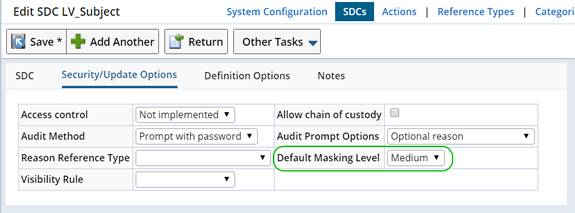
| Default Masking Level | Assign a Default Masking Level for this SDC. Sensitive information is presented to unauthorized Users using the defined Masking Level. |
| View Masked Data Operation |
Upon checking the "Can be Masked?" field in the SDC Definition Options detail, the "ViewMaskedData" Operation is automatically added.
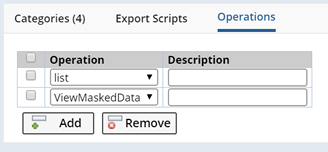
When defining Security Sets or SDC Access for this SDC (or a specific SDI) use this Operation to give Users or Job Types the authority to view sensitive information.
| Access Control Option | Configure the View Masked Data Operation |
| Departmental | Utilizes Departmental Security. Define SDC Access For each authorized User and provide "Member" (M) access to the ViewMaskedData Operation.
This example states that User 1, User 2, User 3, and User 4 can all view the Participant List page when permitted by Security, but only User 1 and User 3 can view sensitive information when Departmental Security permits. Users 2 and 3 can not view sensitive information when viewing Participants. |
| SDI Security | Utilizes SDI Security. Define a Security Set for the SDC or SDI and check the ViewMaskedData Operation for each User authorized to view sensitive information.
This example states that User 3, User 1, User 2 and User 4 can all view the Study, Participant, and Sample List pages, however, only User 3 and User 4 can view Masked Data when displayed. |
Limited Data Access |
Generally, organizations have 2 types of Users. Users who can see sensitive information and users who can not. Access to sensitive information for external Users can differ from Study to Study. As a physician, the same individual could have access to sensitive information in Study A, but as a Research Coordinator, would not have access in Study B. This would require granting that individual a different kind of access for each Study.
Do the following to configure this option:
| 1. | Define a detail table for the Study SDC. This table will be used to determine if an unauthorized user has only Limited Access. | ||
| 2. |
Configure this table as a detail in the Study Maint page.
|
||
| 3. | In the MaskingPolicy, write a SQL query to retrieve this value. The "Limited Data Access SQL" (Advanced Property) can be used to determine the access restrictions for the current User.
|
||
| 4. | This SQL will return a dataset named "sqldataset" which can then be used in the Enable Masking Groovy Expression. For example:
|
Example Configuration |
|
|
The following sections provide example Data Masking strategies and their configuration.
Visibility Determined by Role
|
Two Users within the same department work with Subjects. One User is authorized to view and manage sensitive Subject information, the other can see limited Subject information. The following example describes the necessary steps to achieve this scenario.
User 1 is authorized to view sensitive Subject information. He is given this authority by checking the Role "ViewMaskedData" for his User. As an authorized User he can see all sensitive information.
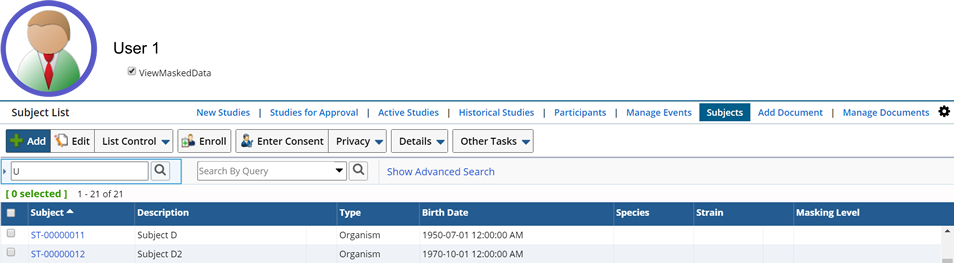
User 2 is not authorized to view sensitive information and is presented limited Subject information.
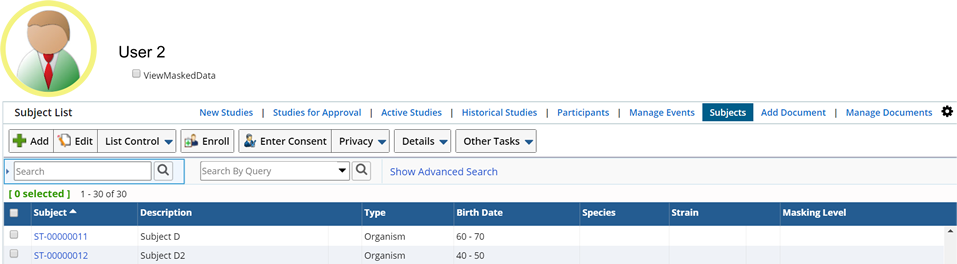
Configure the following to achieve this simple Masking strategy.
Since we are viewing the Subject List page in this example, the Subject SDC is configured as follows:
|
|
In the Definitions detail define the following:
| Option | Description |
| Contains Sensitive Data | Yes (checked) |
| Can be Masked? | Yes (checked) |
In the Security/Update Options detail specify the following:
| Option | Description |
| Visibility Rule | Since the Masking Policy indicates a "Role Only" Visibility Rule the SDC Visibility Rule is not needed. |
| Default Masking Level | Defining a "Medium" Masking Level shows unauthorized Users an age range instead of the Subject's actual birth date. |
The Masking Policy is defined with a Global "Role Only" Visibility Rule, "ViewMaskedData" is the defined Role.

Note that the Medium Masking Level for the Subject SDC specifies that the "birthdt" column should display a 10 year age range in place of the Subject's birth date. The "Date" Data Type is used to define the Masking Logic.
Visibility Determined by SDI Security
|
In Biobanking, Users within different Departments or organizations might share Participants for use in a Study. Users are authorized to view Participant records for each other's Studies, but are only authorized to view sensitive information within their own Studies.
In the following example, Users 1 and 2 are members of Department 1, and Users 3 and 4 are members of Department 2.
User 1 created Study D1 and enrolled a Participant.
User 3 created Study D2 and enrolled a Participant.
When User 1 is the current User, and views the Participant List page, he is authorized to view sensitive information on the Participant record for Study D1 (Department 1), but shown masked Subject information for the Participant of Study D2 (Department 2).
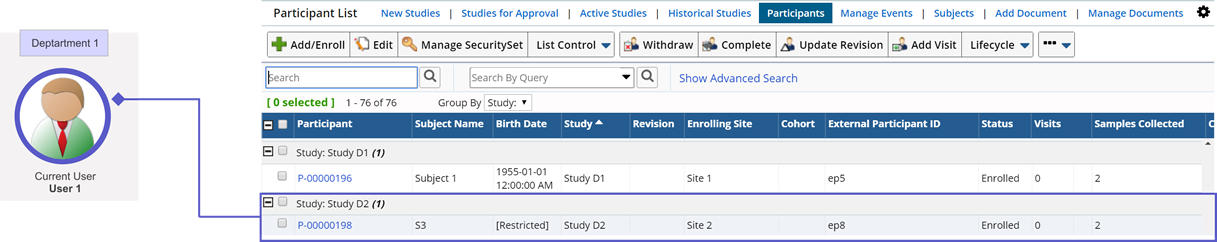
Configure the following to achieve this Masking strategy.
Since we are trying to control the visibility of sensitive information when viewing Participants, we will define a Visibility Rule for the Participant SDC.
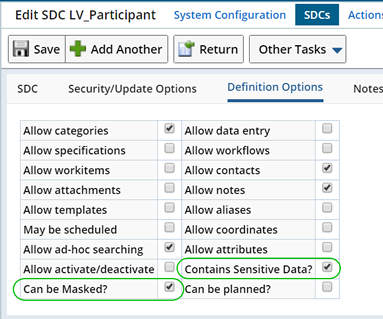
|
|
In the Definitions detail define the following:
| Option | Description |
| Contains Sensitive Data | Yes (checked) |
| Can be Masked? | Yes (checked) |
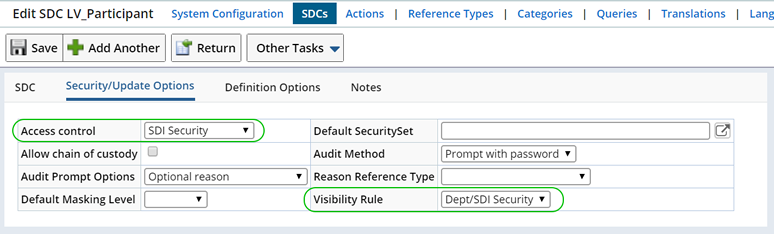
In the Security/Update Options detail specify the following:
| Option | Description |
| Access Control | Choosing "SDI Security" uses existing SDI Security to determine who is authorized to view sensitive information. Users with Access to the SDI will be authorized to view sensitive information. |
| Visibility Rule | Dept/SDI Security will determine the current User's visibility. |
| Default Masking Level | This determines the Masking technique based on the Masking Policy. Since no Masking Level is defined, the global Masking technique is used. |
During Study creation, each Study Coordinator will determine who can view Masked Data for their Study.
Using the Manage Security Set option (Study List page, Manage Security Set button), for each associated SDC, give each User the authority to view Study, Participant and Sample List pages for this Study. For each User authorized to view sensitive information, also check the ViewMaskedData operation.
User 3 defined the Security Set for Study D2 as follows:

Users 3 and 4 (Users within Department D2) are authorized to "ViewMaskedData". Users 1 and 2 are not (ViewMaskedData operation is not checked).
The Global Visibility Rule is defined as "SDC Visibility Rule Only". This defers the visibility decision to the SDC.
Since a Masking Level was not defined at the SDC or SDI level the Global Masking Rules are applied.
Advanced Considerations |
|
|
Before enabling Data Masking review and consider the following:
API Considerations |
Data Masking adds the following API processing:
DataSet.getValue:
| • | If a cell value is masked, then the getValue will return the masked value always. |
| • | An overloaded method of getValue is provided to return the actual value. |
DataSet.sort:
| • | If a DataSet has some cells which are Masked, then sorting on those columns will treat all Masked values the same and will display at the end of the sorted list for an Ascending sort. |
DataAccessService.createRSetQ
| • | If Access Control has been enabled in Query SDC, this method will check if the Query Id being invoked is accessible to the current User or not. |
GetSDI[String/Data/Number] actions:
| • | An additional property enforces Data Masking on the return value for primary column values. |
The LabVantage REST API supports PHI data masking for GET method calls:
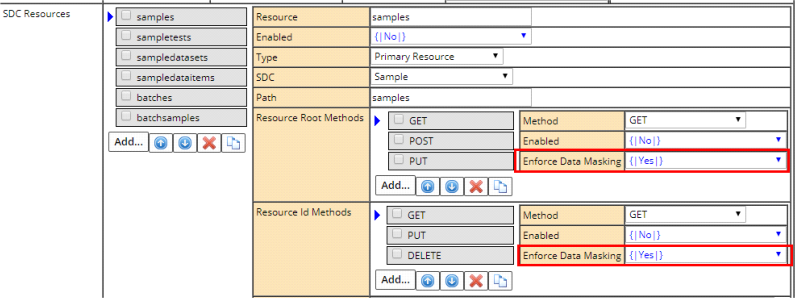
| • | The RESTPolicy provides an option for GET method. |
| • | The property is by default set to "Yes" OOB. |
| • | The property makes sure that the data returned by the REST GET request passes through the Global Data Masking logic as defined in the MaskingPolicy. |
Queries |
Creating Queries that search on columns defined as sensitive in the MaskingPolicy is not recommended. However, if necessary, pre-existing Role based Security can be used to enforce Query access.
Any OOB Queries that allow searching on OOB sensitive columns will be marked with the ViewMaskedData Role. If Data Masking is implemented, simply enable Role based Security on Queries to hide those Queries that search on sensitive columns.
The "Apply Role to Adhoc Queries" property in the Masking Policy will determine visibility in Adhoc Queries. If the current User does not have the appropriate Role (as defined in the "Role" field), the Ad-hoc query tree will disable all those columns marked as sensitive in the MaskingPolicy (Sapphire Custom node). The system will be restrictive in the sense that if a column's maskability is Groovy-based, then Adhoc Query will not allow unauthorized Users to search/display that field.
Similar to Adhoc query, Global Search will not index those columns defined as sensitive in the MaskingPolicy (Sapphire Custom node). This is Global and not User-specific. The "Index Sensitive Data" property in the SearchPolicy will be set to "No" OOB, but can be overridden.
Miscellaneous Considerations |
Before Enabling Data Masking be sure none of the following applies to fields defined as sensitive:
| • | List page column is not set to "Return Value=Yes". |
| • | User buttons should not access this field from the page. If so, change the code to get the value using an Ajax call. |
| • | Ensure this value is not passed into an Action button property. |