Overview
| Top |
|
External Authentication |
Content |
||||||||||||
|
Overview |
|
|
LabVantage External Authentication uses LDAP (Lightweight Directory Access Protocol) to verify contact information from an LDAP server (Directory System Agent).
|
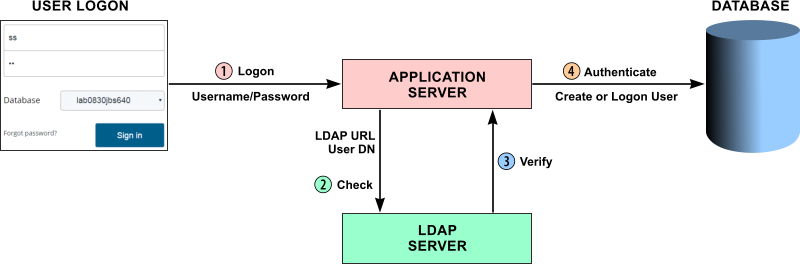
Here is an example of basic External Authentication functionality:
| 1. | When someone logs onto LabVantage, External Validation sends the entered Username and Password to the Application Server. | |
| 2. | The LabVantage Application Server calls the LDAP Server (LDAP URL) and sends it the DN (Distinguished Name associated with the Username) and account defined by the External Validation rules set in the Authentication Property Manager. | |
| 3. | If the DN is defined in the account and the Password is correct, the LDAP server sends a verification to the Application Server. | |
| 4. | The Application Server checks to see if the verified user is a LabVantage User registered in the LabVantage Database. If so, it logs the User onto LabVantage. If not, the attempted logon fails, unless the External Validation rules tell the Application Server to create a new LabVantage User.... in which case, a new LabVantage User is created for the user verified through LDAP authentication. |
These additional configuration features are also available:
| • | When automatically creating a LabVantage User from an LDAP User, LabVantage allows using a specific User Template to create the LabVantage User based on the User's LDAP attributes. |
| • | When an existing LabVantage User logs on through External Authentication, LabVantage can synchronize the LabVantage User's Job Types based on the User's LDAP attributes. |
LabVantage External Authentication has been evaluated with Microsoft Active Directory (does not have anonymous binding) and Oracle Internet Directory (anonymous binding was also evaluated).
References |
|
|
RFC 1777, set forth by the Internet Engineering Task Force, describes the current LDAP specification. The IETF provides access to many other documents concerning LDAP operation and command syntax (such as RFC 2255 for URL format). Visit www.ietf.org for information that is not specific to LabVantage.
Authentication Property Manager |
|
|
The following properties specify External Validation rules. All properties except "Default User To Create" are mandatory.
| Property Name | Description | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Enable LDAP Authentication | "Yes" enables the External Authentication
feature through the LDAP server. A user with an "Authentication Type"
of "Internal" (defined on the User
Maintenance Page) uses LabVantage authentication.
"No" disables the External Authentication feature through the LDAP server and uses LabVantage authentication. The user's "Authentication Type" is ignored.
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Call LDAP for ESignature | "Yes" calls the LDAP Server every time a user
verification is requested during a LabVantage session (such as logon, verification
through Electronic Signature, and so on).
"No" calls the LDAP Server only during logon. Subsequent user verifications (such as Electronic Signature) are based on the single logon password validation, which is used throughout the entire LabVantage session. |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Sync LDAP User Password to LabVantage | By default, LabVantage synchronizes a User's LDAP password with his LabVantage password. This option breaks this association to prevent LabVantage from storing the LDAP password. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| LDAP URL with Base DN | URL of the LDAP Server with the Distinguished
Name of the Directory Information Tree root. This is not a full LDAP URL
that specifies various attributes, a scope, and filter settings. LabVantage
uses this only to find the LDAP Server. Accordingly, use the following syntax
to specify this value:
ldap://host:port/dc where
Example: dc2.hal.com:389/dc=hal,dc=com finds the DNS with hal in the .com top level domain. |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Root User DN | Distinguished Name of a user in the account.
Root User DN and Root User Password (below) are not required if the LDAP
Server allows anonymous binding.
Example: The binding string cn=mobutu,cn=users,dc=hal,dc=com specifies a DN, where:
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Root User Password | Password used by the LDAP Server to verify the person identified by the Root User DN. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| The RDN for the User Search | Relative Distinguished Name used to search
for users in the Directory Information Tree.
You can search for a user in multiple LDAP tree nodes, provided each userid on the LDAP server is unique. To do this, use a double-pipe (||) as separators. For example... cn=users||cn=specialusers,cn=users||cn=people ...searches both the specialusers and people nodes of the users tree. In addition to searching for users LDAP tree nodes defined by this property, LabVantage also searches all subtree nodes for the user if a user is not in the defined node. |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Attribute Name of User ID | Attribute used by the LDAP Server as the logon name of the user. If using Microsoft Active Directory, this would generally be SAMAccountName. The user�s logon name would then be taken from the SAMAccountName attribute. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Secondary LDAP Servers | Allows additional LDAP servers to be defined
with the property "LDAP URL with Base DN". All other properties
for additional servers are assumed to be the same.
The primary server is defined by "LDAP URL with Base DN", which will be the server that authenticates users. If the primary server is not available, a warning message is written to the log, and the next available LDAP server will be used to authenticate users. If all servers are unavailable, an error is generated. The "Test Connection" button indicates a successful connection only if all servers test successfully. "Test Connection" opens a dialog that shows the "Current LDAP Server", which is the server being used for user authentication. |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| LDAP To LV User Mapping | Allows a new LabVantage User to be automatically
created for someone who is verified through LDAP authentication but not
currently in the LabVantage Database, or synchronize LDAP attributes to
an existing LabVantage User on User Logon.
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| LDAP to User Message Mappings | Allows LDAP error messages to be displayed
in a more user-friendly manner:
If these values are not specified, a generic message is issued to maintain backward-compatibility. |
These buttons are available:
|
Saves all changes. |
||
|
Pings the LDAP server and reports a success or failure message. |
Java API |
The BaseAuthentication API provides hooks for customized external authentication
code. The DefaultAuthentication API provides default implementations of the
authenticateUser and createUser methods (but not the synchronizeUser method)
for LDAP V2- and V3-compatible servers.